We Simplify The Complex World Of Industrial Cybersecurity
Our experts are dedicated to helping industrial operations thoroughly understand the benefits and distinctive processes of industrial cyber security. Our mission is to help keep you protected. As facilities rely more and more on connected equipment or systems, which may include remote access, it is important to secure your networks and digital infrastructure.
To help you better understand your operational industrial cyber security needs, we offer assessments and services that provide a more well-rounded, personalized analysis of your situation to take practical steps toward securing your critical infrastructure.
Our Solution Architects can recommend products that combine ease-of-use and security to let you get the most of your connected equipment and data-driven processes.
Schedule An Assessment or Talk To An Expert
The Foundations of Cybersecurity
AutomaTech prides itself on providing industrial companies cybersecurity solutions that offer world-class protection.

- Have a cyber plan & roadmap
- Have a Network Diagram
- Be organized and know where your devices are located

Protect
- Use contemporary firewalls, managed switches, use Linux based solutions
- Segment your OT from your IT networks
- Use and adopt MFA on all systems
- Use virtual machines wherever possible

- Install an OT cyber threat detection system
- Your OT cyber detection systems should work with your DMZs and firewalls

- Develop a robust process and response plan
- Have organized plant to shut-down systems
- Twice annually, validate your back/restore (DR) process
- Have quick process o disconnect and isolate OT network and compute platforms

- Have a plan to restore your OT systems in a defined stat-up sequence
- Validate you are reloading latest versions of your configuration files for VFDs, PLCs, SCADA & other OT systems
How Much Security Do I Need?
Download our brochure to see our risk level vs. cost matrix and learn about the right balance between cost and protection for industrial cyber security.

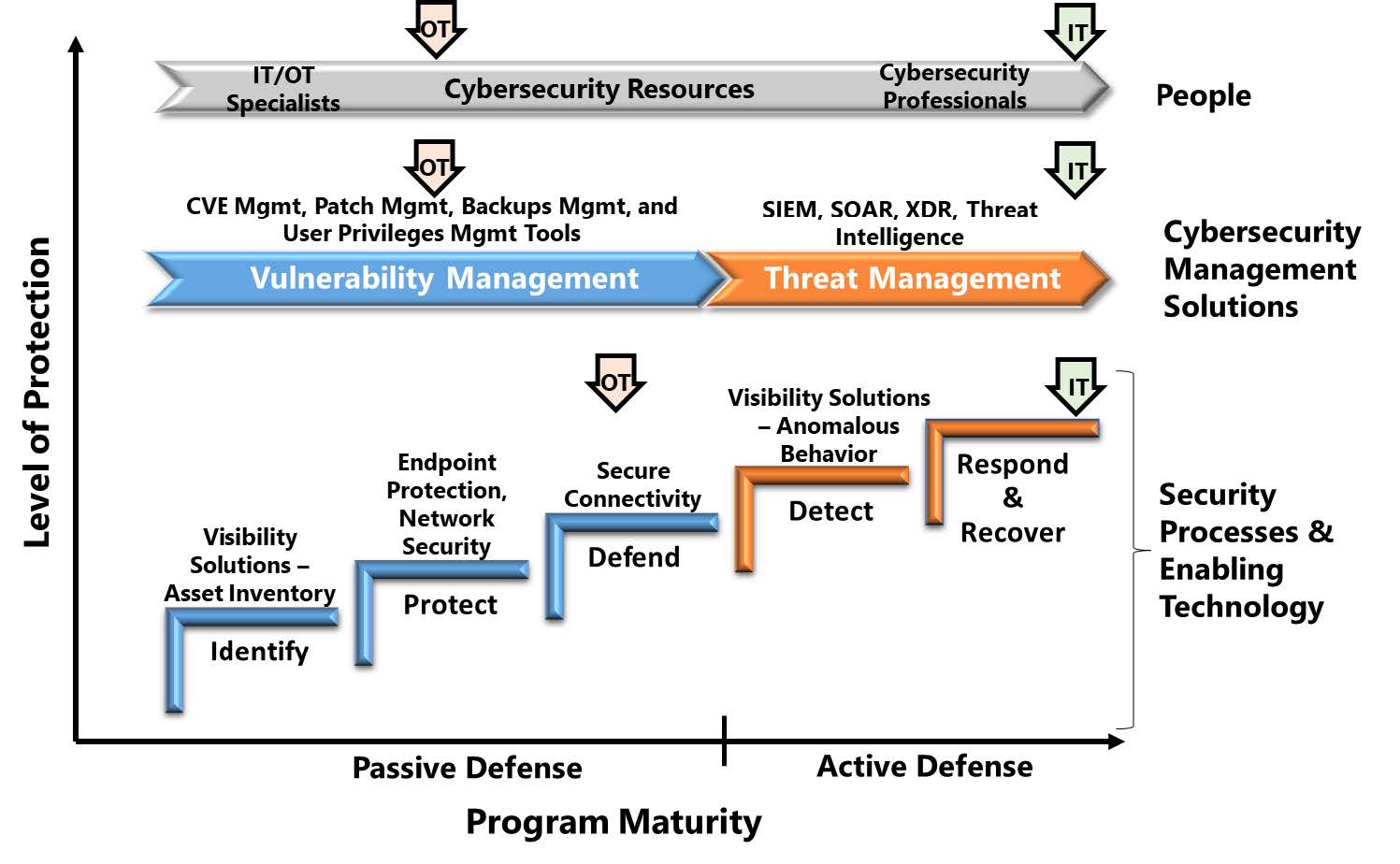
Today’s OT Systems Need IT Security Capabilities
Industrial companies require stronger OT cybersecurity programs to deal with today’s sophisticated threat environment. Managers need to invest in more advanced cybersecurity capabilities that can enable active defense of critical operations. Download this ARC report describing the major gaps in today’s OT cybersecurity programs and what’s needed for today and tomorrow’s more challenging threat environment.
Read What Our Customers Say

Operation protected a Critical Remote Facility with a platform that monitors, identifies, and captures unauthorized access attempts.

Regional Utility Provider secured off-site control systems, which saved personnel from making long drives to the facility to troubleshoot issues.

Owner eliminated hundreds of network devices, reduced deployment times & staffing requirements. Realized tremendous savings.
Our Trusted Partners